
Cybereason and Motorola Mobility: Real-Time Network Visibility
The Cybereason MalOp (malicious operation) detection engine allowed a single Lenovo analyst to manage up to 200,000 endpoints, almost three times their current network needs...
Cybereason Team
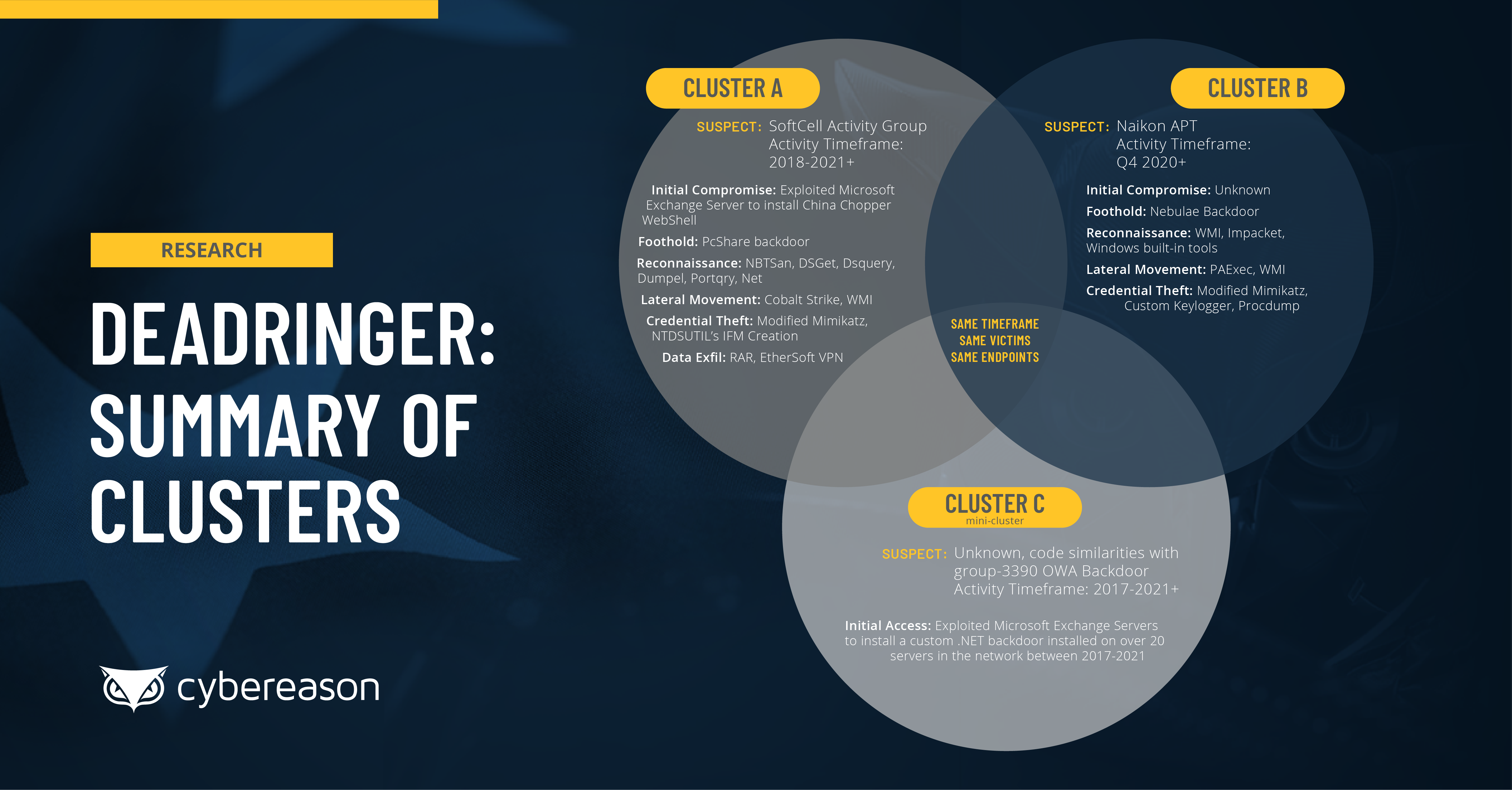
The Cybereason Nocturnus Research Team recently released a major threat intelligence research report titled DeadRinger: Exposing Chinese Threat Actors Targeting Major Telcos, which details the discovery of several previously unidentified attack campaigns targeting the telecommunications industry across Southeast Asia, where several clusters of attack activity were identified and assessed to be the work of several prominent APT groups who are known to conduct operations aligned with the interests of the Chinese government.
Date: August 12th, 2021
Time: 1:00 PM ET / 10:00 AM PT
REGISTER HERE
Join this webinar to hear analysis of the espionage operations, including:

Cybereason is dedicated to partnering with Defenders to end attacks at the endpoint, in the cloud and across the entire enterprise ecosystem. Only the AI-driven Cybereason XDR Platform provides predictive prevention, detection and response that is undefeated against modern ransomware and advanced attack techniques. The Cybereason MalOp™ instantly delivers context-rich attack intelligence across every affected device, user and system with unparalleled speed and accuracy. Cybereason turns threat data into actionable decisions at the speed of business.
All Posts by Cybereason Team-1.png)
Assaf has over 15 years in the InfoSec industry. He started his career in the Military forces where he developed extensive experience in offensive security. Later in his career he led Red Teams, developed penetration testing methodologies, and specialized in malware analysis and reverse engineering.
-1.png)
Mor Levi has over 8 years of experience in cyber investigations, incident response, and SIEM/SOC management. She began her career as a team leader in the Israeli Defense Force security operation center. Later, she led an incident response and forensics team at one of the big four accounting firms providing services to global organizations.

The Cybereason MalOp (malicious operation) detection engine allowed a single Lenovo analyst to manage up to 200,000 endpoints, almost three times their current network needs...

The Los Angeles branch of Planned Parenthood was hit with a ransomware attack that risks exposing sensitive and potentially life threatening information on 400,000 patients...

The Cybereason MalOp (malicious operation) detection engine allowed a single Lenovo analyst to manage up to 200,000 endpoints, almost three times their current network needs...

The Los Angeles branch of Planned Parenthood was hit with a ransomware attack that risks exposing sensitive and potentially life threatening information on 400,000 patients...
Get the latest research, expert insights, and security industry news.
Subscribe